Monitoring and Blocking Data Exfiltration With DLP + IAM Conditions
Data exfiltration Data exfiltration has risen as one of the most prevalent and disruptive security incidents in today’s cloud systems. A bad insider, a compromised identity, too permissive of an access path that someone stumbled into accidentally – whatever the cause, the effect is that sensitive data leaves the environment improperly. As we’ve seen with the proliferation of distributed teams, multi-cloud and the myriad SaaS integrations available to organizations, the attack surface for inadvertent or malicious misuse has expanded significantly.
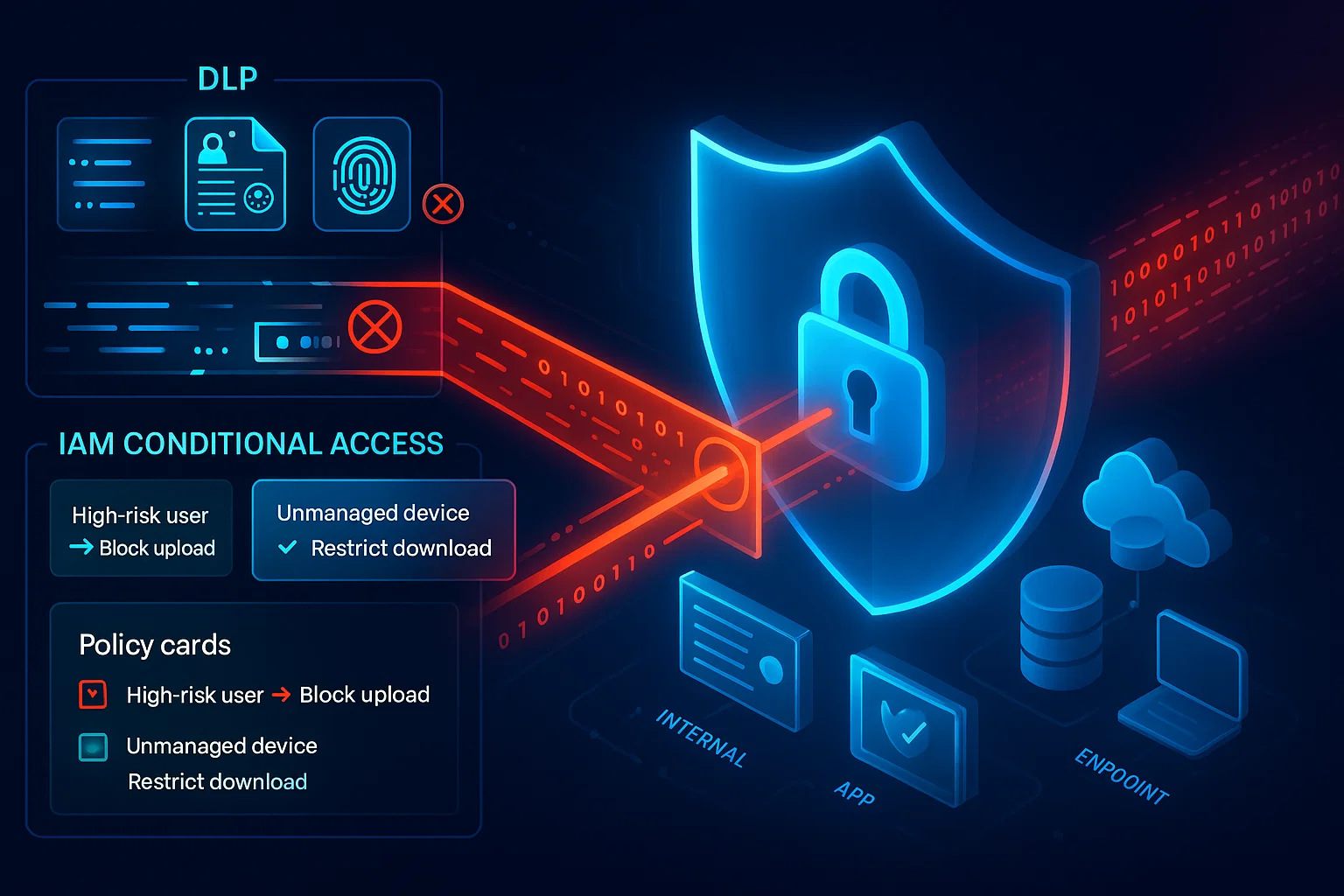
That’s where bringing together data loss prevention (DLP) with IAM Conditions begins to gain a lot of appeal. Each technology does something interesting on its own — DLP helps you find sensitive data, and IAM Conditions gives you context-based access control. But when we combine those, they’re something much more potent — real time monitoring and adaptive access controls with realistic guardrails that are automatically enforced to let you stop exfiltration before it’s a headline.
It’s particularly effective in cloud environments like Google Cloud since there are native, integrated tools (GCP DLP, VPC Service Controls, IAM Conditions) to build defenses around data. Rather than slapping a dozen third-party controls on top, you can rely on security layers that already know your identities, workloads and data flows. That’s big — it has the side effect of helping out with accuracy as well as computational simplicity.
Why Data Exfiltration Is Harder to Stop Than Most People Think
Data exfiltration prevention looks simple on paper: block sensitive data from leaving environments where it doesn’t belong. But in practice, it’s far more complex because of how cloud environments behave. Here are a few reasons:
- Identity is everywhere. Cloud systems rely heavily on service accounts, machine identities, workloads, and automation pipelines. Any one of those can be misconfigured and unintentionally leak data.
- Data is fluid. It moves between storage, analytics platforms, logs, backups, and SaaS applications. Traditional perimeter-based controls don’t see this movement.
- Insider threats exist. Not necessarily malicious ones — sometimes well-meaning employees download reports to work offline or sync data into personal tools without realizing the risk.
- Outbound pathways are abundant. Public APIs, cloud storage buckets, SaaS connectors, browser uploads, script automations — the number of possible exit points is huge.
That’s why cloud DLP monitoring alone is not enough. And IAM alone doesn’t know the sensitivity of the data it’s protecting. But together, they create a layered defense that is far harder to bypass.
How DLP Helps With Data Exfiltration Prevention
At the heart of any exfiltration defense strategy is knowing what you’re protecting. Cloud DLP tools, such as GCP DLP, help by:
- Discovering where sensitive data is stored
- Classifying data based on content and patterns
- Scanning for PII, PHI, financial details, or custom-defined identifiers
- Monitoring data access behaviors over time
- Triggering alerts when high-risk data moves to unexpected destinations
The biggest advantage of cloud-native DLP tools is that they operate close to your data stores. Instead of relying on endpoint agents or network taps, they can analyze data in storage, streams, databases, and even logs.
When configured correctly, cloud DLP monitoring establishes a baseline: what normal data access looks like, what risky behavior looks like, and where your most valuable data sits. Once you have that visibility, controlling access becomes far easier.
Where IAM Conditions Strengthen Security
IAM Conditions allow you to evaluate context before granting access. This includes:
- User identity
- Device trust level
- Time of day
- Geographic location
- Network origin
- Access pattern or request type
The beauty of IAM Conditions security policies is their flexibility. You can say:
- “This service account can only read data from this bucket when the request originates from the VPC.”
- “This user can only access sensitive data during business hours.”
- “This role cannot download data unless the device meets security posture requirements.”
By integrating contextual signals, IAM Conditions ensure that even if a credential is stolen, it can’t be used freely. The attacker would need to meet all contextual requirements — and that’s extremely hard without being inside your trusted boundaries.
Why the Combination Matters
DLP tells you what is sensitive.
IAM Conditions tell you when access is appropriate.
Together, they tell you who should be allowed to touch sensitive data and under what conditions — and they enforce it automatically.
This pairing creates three major advantages:
1. Automated Protection
When DLP classifies data as sensitive, you can automatically apply more restrictive IAM Conditions to it.
For example:
- If a storage bucket is identified as containing medical information, IAM Conditions can lock it down to approved devices only.
- If a BigQuery table contains financial data, download operations can be denied entirely.
No manual intervention needed.
2. Prevention Instead of Detection
Traditional DLP often reacts after access happens. But when tied to IAM Conditions:
- Risky requests are blocked before data moves
- High-risk behavior triggers immediate access restrictions
- Sensitive data is automatically segmented into more secure zones
This drastically reduces the window of exposure.
3. Stronger Insider Threat Control
Insiders — intentional or accidental — are harder to detect with traditional tools because their access often appears legitimate. But DLP + IAM together look for context, not just identity.
Examples:
- If an employee suddenly downloads gigabytes of data outside work hours, IAM can block the request.
- If a user uses a device that fails posture checks, access to sensitive data can be revoked instantly.
- If an engineer tries to move sensitive data to a personal Google Drive, the action gets denied at the API level.
This is how cloud environments turn visibility into control.

Practical Architecture for Blocking Exfiltration
A well-structured cloud exfiltration prevention setup usually includes:
1. Data Discovery and Classification with DLP
- Scan all storage sources
- Classify sensitive datasets
- Apply labels/tags based on sensitivity
- Set up continuous DLP scans for drift
2. Segmentation of Data and Identities
- Separate highly sensitive datasets into dedicated storage
- Use service accounts with narrowly defined scopes
- Limit cross-environment access paths
3. IAM Conditions Policies
Create contextual access policies such as:
- Device-based conditions
- Time-based access
- Network boundary requirements
- Service account download restrictions
- Conditional tokens
4. VPC Service Controls (Where Applicable)
Lock sensitive data inside controlled perimeters:
- Prevent copying to external buckets
- Deny access from untrusted networks
- Force API calls to originate from the protected zone
5. Automated Response
When DLP detects risky patterns:
- Quarantine service accounts
- Disable download permissions
- Trigger alerts to SOC/NOC teams
- Enforce stricter IAM policies dynamically
6. Continuous Monitoring
Set up real-time data movement alerts using:
- DLP findings
- Access logs
- IAM audit logs
- Cloud monitoring dashboards
Combined, these pieces create a living, adaptive security perimeter around your sensitive information.
Common Mistakes to Avoid
Many organizations try to implement DLP or IAM-based protection but run into issues because of misconfigurations. Here are typical traps:
- Relying only on static IAM roles instead of contextual IAM Conditions
- Scanning data once instead of enabling ongoing DLP monitoring
- Over-granting service accounts with broad permissions
- Ignoring data movement between internal services
- Not enforcing VPC perimeters for sensitive data projects
- Treating insider threats as rare events, rather than designing controls around them
Avoiding these mistakes saves a lot of time and reduces the blast radius of incidents significantly.
Conclusion
The problem with data exfiltration is not a single one — it’s a chain of weaknesses that fit into place: too many permissions, no visibility, poor segmentation or devices accessing data they shouldn’t. The joint use of GCP DLP and IAM Conditions can help fill these gaps in an organized manner. DLP provides visibility into sensitive information, while IAM Conditions establish access guardrails based on context.
Together, they deliver a proactive, extensible and cloud-native data exfiltration prevention approach. Instead of reactive alerts or manual investigations, you receive proactive monitoring, real-time blocking and a powerful insider threat control model at no additional charge built throughout the cloud fabric.
If you intend to reinforce your strategy for cloud DLP monitoring this combination must be the cornerstone of your architecture. It is one of the best ways to limit access, minimize data loss and retain trust in an environment in which insider threats and credential-based breaches are mutating.
Recent Posts
- The Real Reason IT Backlogs Keep Growing (And How to Fix It)
- The Real Differences Between Application-Layer Firewalls Across Vendors
- Optimizing Roaming and Low-Latency Handoffs in Aruba 6GHz Wi-Fi Deployments
- Monitoring and Blocking Data Exfiltration With DLP + IAM Conditions
- Implementing Role-Based Access Control (RBAC) With ClearPass Policy Manager
Recent Comments
- ISO 27001 Certification Audit on The Impact of Quantum Computing on Cybersecurity: Preparing for the Future
